How Community and Curiosity Turned a Software Engineer into a Penetration Tester

Hi! Can you introduce yourself and describe your current role?
My name is Makayla Ferrell. I currently work as a penetration tester for a leading government contractor. I perform penetration tests, red teams, and vulnerability assessments on government systems. These tests can range from physical assessments to web applications to networks with over 10,000 hosts. I like to joke that as an ethical hacker, I can hack the government and not get arrested.
What’s your backstory and how did you first get into cybersecurity?
During my first summer of college, I did like most computer science majors and applied to all the internships I could. I got an internship as a cybersecurity analyst for a credit union in my hometown. I was doing mostly firewall rules, SIEM reporting, and some inventory management. I did not find the work interesting and decided cybersecurity was not for me. However, I did meet some great people and obtained my Security+ during the internship.
During sophomore year of college, I received the DOD SMART scholarship. As part of the scholarship, the DOD pays for your education and in exchange, you agree to work at your matched DOD facility after graduation. I requested and was matched as a software engineer with the Army Software Engineering Center. My work focused on programming embedded systems and web applications. During my time as a software engineer, we had regular code reviews and penetration tests. I was interested in how the security team found vulnerabilities and decided to do more research into cybersecurity. I found BlackGirlsHack, which is an amazing nonprofit that helps people get into cybersecurity. They sponsored me to go to DEFCON and introduced me to more cybersecurity professionals. At DEFCON, I participated in a few big CTFs, and realized that I enjoyed the problem-solving of hacking more than I enjoyed programming.
Luckily, you can easily move around at the Army Software Engineering Center, so I requested to switch to our penetration testing team. I started with writing scripts for the team and helping to automate their process. It was an easy way to use my programming background while I learned more about the penetration testing process. After scripting and shadowing a little bit, I became a penetration tester.
How has your software engineering background benefited you in your current role as a penetration tester?
One of the things I learned during my transition into cyber is how much cybersecurity is left out of the computer science curriculum. Most programs don’t include secure coding courses, so as a programmer, you are taught to think about efficiency and passing test cases but not security. Code reviews on most development teams focus on efficiency, (i.e. time and resources). If I were a programmer now, I would write way more secure code because I have been exposed to security training, but the everyday programmer has not. I hope this changes in the near future, but I always keep it in mind in my penetration tests.
I think my background in software engineering provides me with more perspective and things to think about during a penetration test because I know how a programmer would approach an issue. When doing a pentest, especially on new systems, I always think about what I would do if I was a programmer just trying to make it work efficiently to pass a peer review. Once I have thought about that, then I think about how that would create security flaws. For example, a developer trying to update customer data will just call the update API and not think about whether to sanitize the data or authenticate the user again.
In my opinion, aspiring penetration testers do not need to learn to code or computer science fundamentals. However, they should learn a scripting language and understand how to execute commands like PowerShell. I think the more knowledge, the better, so if they have the time and are interested, then 100% go for learning to code and computer science fundamentals. However, if I were an aspiring penetration tester, I would get a firm grasp on a scripting language like Python and make a port scanner before I would learn to code applications or learn Dijkstra’s algorithm.
I have noticed an overlap between software engineering and penetration testing, but I think it is role-specific. I was in an application security role that did a lot of manual code reviews and pre-production tests, so I would use my programming background a lot. However, in my current role, which is not specific to application security, I very rarely see the overlap.
What advice would you give to an aspiring penetration tester?
My main advice would be:
- Join a community! BlackGirlsHack was the main reason I made the transition into cybersecurity. They introduced me to amazing people who helped advance my career, free certification programs, and job referrals. Find a cybersecurity community that aligns with you. There are many great ones out there! The people you meet in these communities are likely in a similar position and can help support you through your journey. These communities also have mentors who can offer even more personalized support.
- I always say TryHackMe before HackTheBox. I think it's better to start with a guided introduction than to do HackTheBox and feel defeated because you couldn’t get a flag. I would recommend doing some walkthrough TryHackMe rooms or a learning path, then doing a CTF room in TryHackMe and reading the writeups only when you get stuck. Then when you feel comfortable, test your skills in HackTheBox.
- Don’t cram for the certification. The information from the certifications will be useful so try to really learn the material rather than cramming and forgetting it a week after the exam. They really do use those questions in interviews.
As for certifications I recommend, I think eJPT is often forgotten about, but it is a great beginner certification with detailed course material. Actually, all of the eLearnSecurity exams are very realistic, in my opinion, to things you might encounter in a pentest, and the relaxed time frame compared to OSCP makes it more accessible for people just starting out.
What are your favorite tools to use on an engagement? Have you utilized AI at all in your role?
My favorite tool to use for engagement is Burp Suite. It’s so powerful! Other than Burp Suite, EyeWitness, BeEF, Nuclei, and Cobalt Strike are my goto tools. Eyewitness is a tool to screenshot a large group of webpages and create a report to easily see what's on each of the webpages. This is especially helpful for large pentests when you probably don’t have time to check each individual host to see what kind of webpage it is. Beef is an exploitation framework where you can inject a hook.js script into a webpage and then have a persistent callback from the user's browser. If you have an injection vulnerability, BeeF can raise the severity and is a lot of fun to use. The hook can be used for a bunch of stuff, like turning on a user's webcam or logging their traffic. Nuclei is a web application vulnerability scanner with templates for common vulnerabilities. It's a very useful tool on a web application test, and saves a lot of time. Cobalt Strike is another great and powerful tool, but it has a learning curve if you are used to Metasploit.
As for physical tools, a WiFi Pineapple and a Hak5 rubber ducky can get you very far. If you have ever heard a security professional say, “If you leave a USB on the ground, someone will pick it up and plug it in,” sadly, that is true. Especially, if you put the company logo as a sticker on the USB.
I use AI mostly for writing reports and finding flags for Linux commands. When I am not sure of a good remediation recommendation or which flags will give me the desired output, ChatGPT is great for coming up with those. Unfortunately, I cannot use AI for much more than that, because of my work with the government.
How has being active in the infosec community impacted both your personal and professional life?

Being active in the InfoSec community has helped my professional life through networking and learning from others. I have learned many new methodologies or exploits from being active in the community. There are so many different ways to reach the same goal in hacking and learning other people's approach is always interesting. Most of the open-source tools I use are from someone at a conference or CTF who shared their tools with me.
Being in the InfoSec community has also given me a lot of opportunities to advance my career. It has given me speaking opportunities, the chance to coach a CTF team for a community college, and access to certification programs I never would have known existed.
It has helped my personal life by showing me there are more diverse people in the profession than I see in my workplace. At the Army Software Engineering Center and at my current position I am the only woman on my team. Meeting other women in the field through the infosec community has made it so much easier to feel like I belong in my workplace.
Congratulations on earning your advanced computer science degree from Georgia Tech! What inspired you to pursue this degree, and how was your experience in the program?
I was a peer tutor and teaching assistant in undergrad and loved it. I was also in an undergraduate program with very few women or people of color in the teaching staff and computer science graduating class. I decided to become a professor in the future, so I could help the diversity gap and make computer science more accessible for people like me. Since I was a DOD SMART scholarship recipient, I had to start working after graduation and needed a part-time graduate school program.
I was accepted into two MS in Computer Science programs: Columbia and Georgia Tech. The deciding factor that pushed Gtech over Columbia was the class offerings. Georgia Tech has AI for robotics, natural language processing, machine learning for trading, and so many other interesting electives that I was able to take as a part-time student. It was also considerably cheaper.
Outside of work, what hobbies or interests help you unwind and maintain a healthy work-life balance?
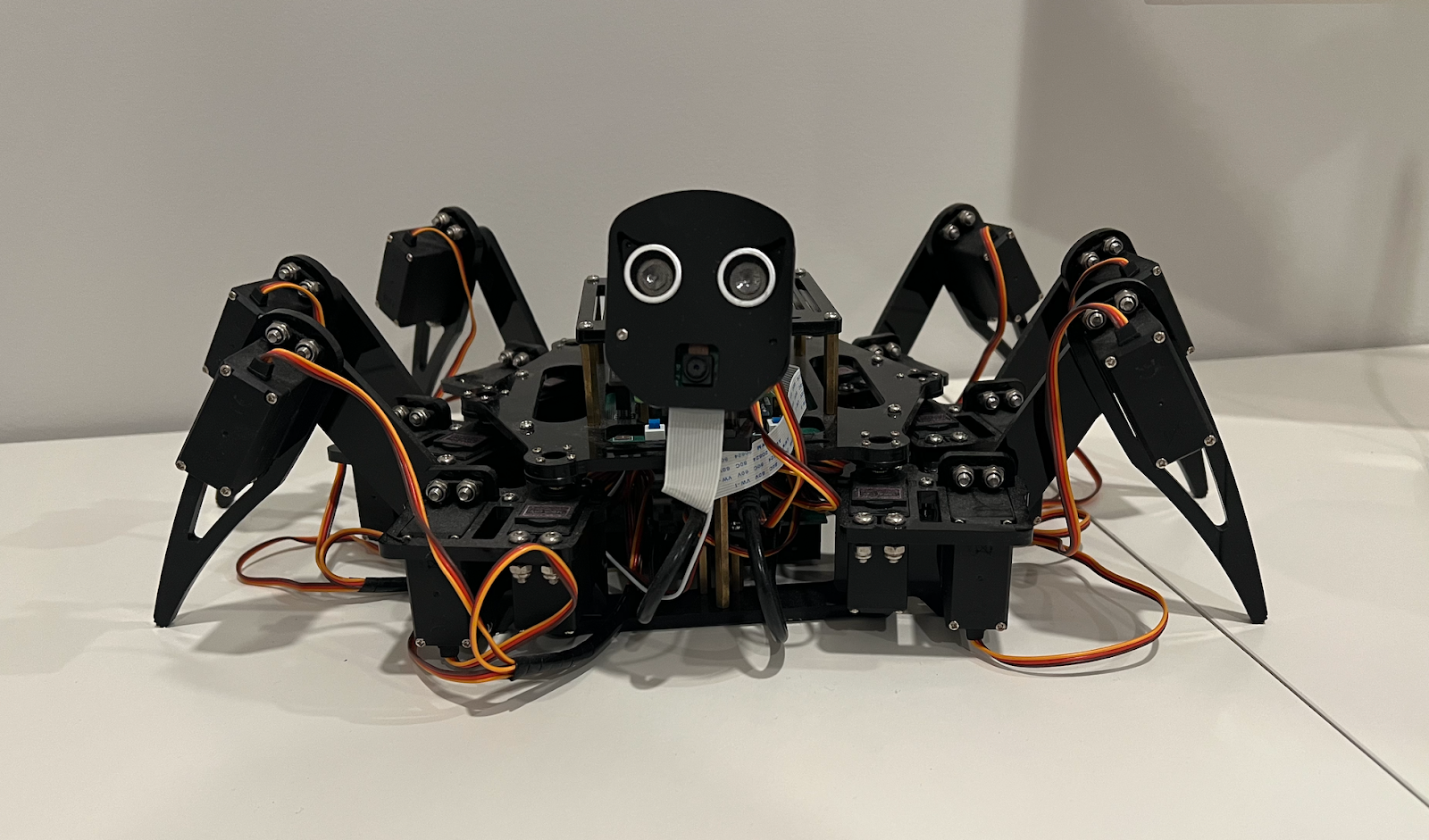
I love robotics. I have a bunch of robots that I have built around my house. I have a spider named Spidey, and he actually understands commands in ASL using a machine-learning model I built for one of my graduate classes.
I teach programming and robotics to middle school and high school girls through BrownGirlsCode.
I love traveling. I’ve been to over 25 countries, and have lived in the UK for a bit. My favorite places are Switzerland because skydiving over the Swiss Alps is beautiful, and Thailand because I love elephants.
I am currently re-learning Mandarin Chinese and meeting with a group to practice twice a week. I originally learned mandarin in middle school and then stopped speaking it until a few years ago. I am currently preparing for the HSK5 exam.
I was a cheerleader in college, and after graduation, I wanted to keep performing, so I auditioned to be a professional cheerleader for the Baltimore Blast soccer team. I was a professional MASL cheerleader for two seasons and had a fantastic time. Now, I am retired from cheer and regularly attend dance classes for fun and to stay active.
Lastly, where can people connect with you or follow your work online?
My LinkedIn: www.linkedin.com/in/makayla-ferrell
My IG: makayla.ferrell
Wrapping Up
Thanks for reading! We are always looking to improve the platform and love receiving feedback from readers. Feel free to send a message on LinkedIn or Twitter.
We sell mugs and comfy clothing guaranteed to please your inner hacker. Check it out at https://shop.jasonturley.xyz/
- Click here to share on Facebook
- Click here to share on Twitter
- Click here to share on LinkedIn
Member discussion